To prevent spam users, you can only post on this forum after registration, which is by invitation. If you want to post on the forum, please send me a mail (h DOT m DOT w DOT verbeek AT tue DOT nl) and I'll send you an invitation in return for an account.
Checking deviations in execution flow of a software process
Hello everyone
I am working on a research project. Having a software system in which I have integrated the logging system by using the database queries that logs every action in the software systems when something happens or something changes in the software like any action performed.
What I want to do is that I have original process model of that software in the form of paper and I want to know that if there is deviation made from that process madel by any of the hacker or someone like developer intentionally modified or bypassed the real execution flow of that software working. In process mining I guess it is called conformance checking.
I will extract the logs of that software system and I will use them as input for prom and generate process model from it. In this way I will get what the software is doing. On the other hand I have the original version of that software process model in the form of a paper.
My question is can I compare the original process model and the process model generated by the software logs. If yes then what will be the strategy to check that so that I may know the deviations done in the software system by developer or any hacker that has bypassed the execution flow.
I apologize for long explanation but it will clear the question that what am I doing and what I want to do.
Any help will be greatly appreciated. Thanks.
I am working on a research project. Having a software system in which I have integrated the logging system by using the database queries that logs every action in the software systems when something happens or something changes in the software like any action performed.
What I want to do is that I have original process model of that software in the form of paper and I want to know that if there is deviation made from that process madel by any of the hacker or someone like developer intentionally modified or bypassed the real execution flow of that software working. In process mining I guess it is called conformance checking.
I will extract the logs of that software system and I will use them as input for prom and generate process model from it. In this way I will get what the software is doing. On the other hand I have the original version of that software process model in the form of a paper.
My question is can I compare the original process model and the process model generated by the software logs. If yes then what will be the strategy to check that so that I may know the deviations done in the software system by developer or any hacker that has bypassed the execution flow.
I apologize for long explanation but it will clear the question that what am I doing and what I want to do.
Any help will be greatly appreciated. Thanks.
Comments
-
Hi,
The best approach would be to model the 'paper process model' as a petri net. Then you can import this in ProM and replay the data over this model. Deviations will then be detected and can be analysed further.
The plugin you're looking for is 'replay log on model for conformance analysis' (or something very similar).
Hope this helps.
Joos Buijs
Senior Data Scientist and process mining expert at APG (Dutch pension fund executor).
Previously Assistant Professor in Process Mining at Eindhoven University of Technology -
Thanks you very much @JBuijs you are always there for help.
In which software should I model the petrinet, in cpn tools or any other alternative is there????
Morover I have already tried modeling that paper model in CPN tools. I am having difficulty in modeling conditions in petrinet since there are many condition checks in the real model. Requested to please suggest any source from which I could know the modeling of conditions/ checks in petrinet.
Once again I am very much thankful for the response. -
If you are considering 'normal'/'vanilla' petri nets I suggest WoPeD.
If you are considering conditions on data attributes for instance @fmannhardt might be of help
Joos Buijs
Senior Data Scientist and process mining expert at APG (Dutch pension fund executor).
Previously Assistant Professor in Process Mining at Eindhoven University of Technology -
In the DataPetriNets package there is a simple editor for Data Petri nets (DPNs). You invoke it in ProM with "Create DPN" or similar. It is based on a simple domain specific syntax and supports basic editing via context menu. It will create Data Petri nets, which you can use for conformance checking, e.g., with the Multi-perspective Explorer:
https://fmannhardt.de/blog/multi-perspective-process-explorer-mpe
However, if you have trouble modeling it in CPN, then DPNs, would not help much. Both allow conditions on transitions. In CPN via colored tokens and local data attribute, in DPN via global variables.
-
@fmannhardt The software is using conditions like if value is for example 1 then go this way and if value is 2 then go that way.
Which PetriNets will he suitable for it.
I was happy with earlier answer of @JBuijs but second comment confuses me. The vanilla PetriNets term and Data PetriNets both are new for me. I have came across term PetriNets so far. :-\
So if I haven't worked on CPN tools, I would not be able to do that. Is it? :-( -
In 'normal' Petri nets you only have places, transitions, arcs and tokens. There are no guards, data, attributes, etc. etc.
In the reply of Felix Petri nets are extended with exactly what you need: attributes, guards, etc.
CPN Tools (CPN = Colored Petri Nets) support petri nets with data as well, but as Felix mentioned in a slightly different way.
Joos Buijs
Senior Data Scientist and process mining expert at APG (Dutch pension fund executor).
Previously Assistant Professor in Process Mining at Eindhoven University of Technology -
Hi,
I think it is better to first have a look at what types of Petri net are really needed to model the so-called paper format process. What types of information are included in the pre-defined process?
I am also curious about you logging. what does actions mean in you log? user operation level or program (like method invocation) level. Does the condition or data aspects are also included in your log?
-
@CongLiu No. Conditions are not included in log. I log operation only. Like updated something, ran some algorithm in that software and and at each step of algorithm I am using a query to insert in the db. Like the execution of the algorithm depends upon the values entered by the user or computer at runtime.
I also want to include conditions in it BTW. Which PetriNets should I use then. -
If you use conditions, both data Petri net suggested by Felix and colored Petri net suggested by Joos can express conditions. But before you make you own choice, be sure to be very careful that the selected model really suits you requirement.
-
@CongLiu @JBuijs and @fmannhardt For explicit clarification, Here is the workflow to which i want to convert to Petrinet and this all is being done in software as well and its logging is being made. And check if this whole workflow or any of its step was skipped.
Please suggest which patrinet should i go for to convert it. And check deviations.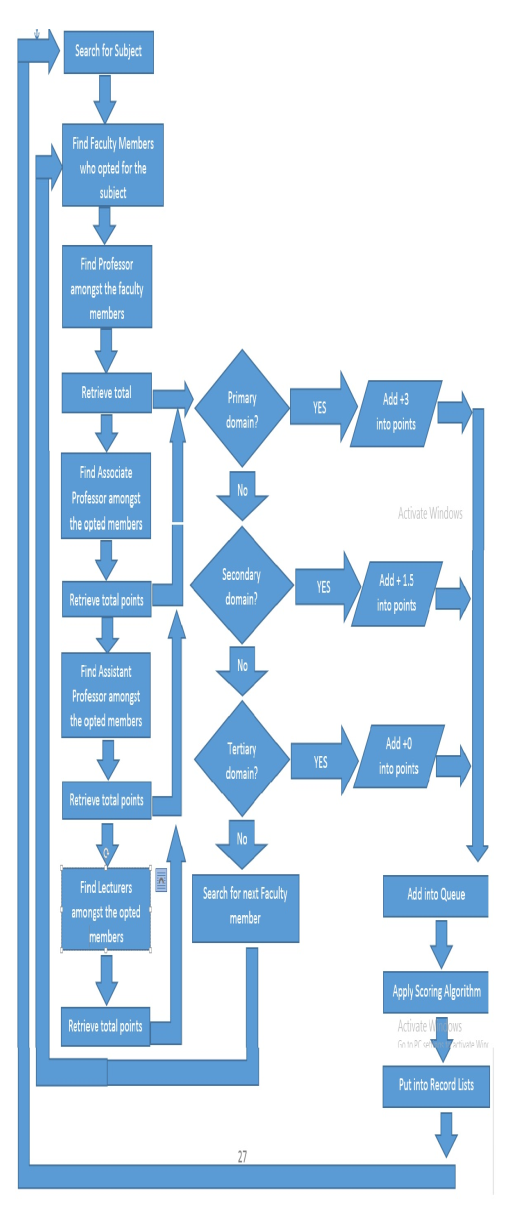
-
Did you try both the DPN editor and further CPN modelling? I would start with DPN since it is better connected with process mining. It seems that it should fit.
Joos Buijs
Senior Data Scientist and process mining expert at APG (Dutch pension fund executor).
Previously Assistant Professor in Process Mining at Eindhoven University of Technology -
No. I was waiting for ur suggestion. That what method should I use CPN tools or DPN? Can this model be made with CPN tools for generating logs.
-
If you want to simulate the model, then, CPN tools would be the most flexible way. There is some information on how to get XES logs from CPN tools here:
http://www.processmining.org/tools/promcpn
(there is also an easier variant without the ProMImport tool, but I cannot find the documentation for that)
Another option would this tool by KU Leuven:
https://lirias.kuleuven.be/bitstream/123456789/458325/1/KBI_1417.pdf
I gave never tried that, but it looks more user friendly.
Anyway, I if you want to to conformance checking and use ProM. I would advise to just to both. Model it as DPN, CPN, etc.
The process does not look so complicated and you will learn something
-
Thank you @fmannhardt i will give it a try.
-
@JBuijs I have created the simplified model in CPN tools and also generated event logs from software. Exported CSV from database and converted to MXML. in Prom I simulated the logs using alpha algorithm. It generates model. Now I have real model in PNML format and I want to run event logs over it.
As mentioned in your first comment that "The plugin you're looking for is 'replay log on model for conformance analysis' (or something very similar)."
I tried to find in Prom plugin. But could not find it . can you please tell me the exact name of the plugin. I am in the final step where i have logs and paper model now in the form of PNML. and want to run logs over it to find the deviations.
At this stage. I am only considering the deviations form the original model whether any step was skipped in software for any specified case.
-
Nothing else. I only want to check if in any specific case from generated logs, any single step of original process model was deviated /skipped. And I want to point out that case.
-
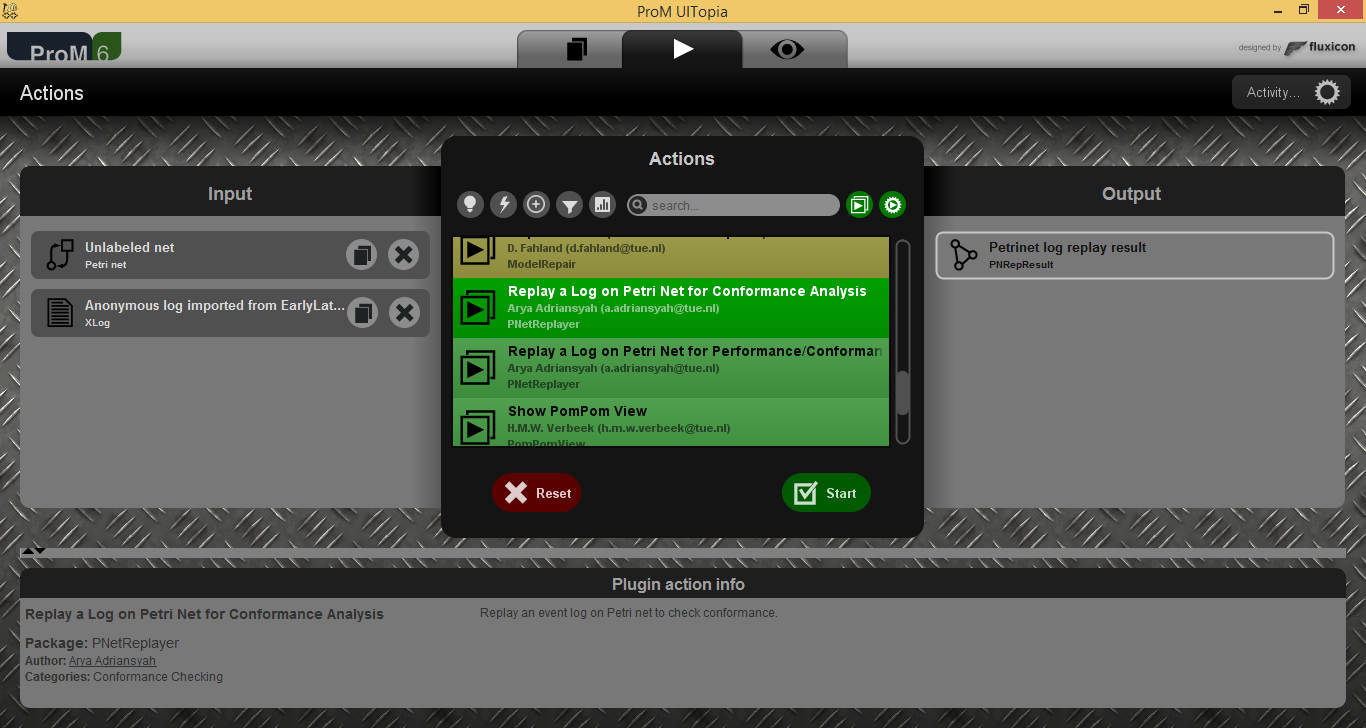
Joos Buijs
Senior Data Scientist and process mining expert at APG (Dutch pension fund executor).
Previously Assistant Professor in Process Mining at Eindhoven University of Technology
Howdy, Stranger!
Categories
- 1.6K All Categories
- 45 Announcements / News
- 225 Process Mining
- 6 - BPI Challenge 2020
- 9 - BPI Challenge 2019
- 24 - BPI Challenge 2018
- 27 - BPI Challenge 2017
- 8 - BPI Challenge 2016
- 68 Research
- 1K ProM 6
- 394 - Usage
- 288 - Development
- 9 RapidProM
- 1 - Usage
- 7 - Development
- 54 ProM5
- 19 - Usage
- 187 Event Logs
- 32 - ProMimport
- 75 - XESame

